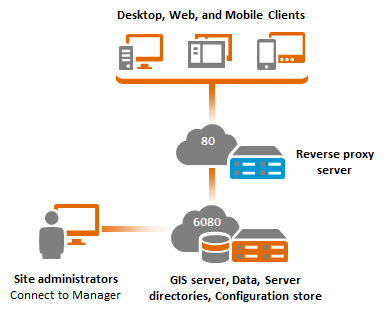
This deployment is a variation of the single-machine deployment where a reverse proxy server is added to the site. A reverse proxy server acts as an intermediary for client requests seeking resources from your ArcGIS Server site, adding extra security features to your site deployment.
ArcGIS Web Adaptor is a reverse proxy implementation from Esri that you can configure in most common web application servers. Alternatively, you can choose to leverage other third-party reverse proxy web servers.
As depicted in the diagram below, ArcGIS Web Adaptor or a third-party reverse proxy server is typically configured on a separate web server machine, although it is also possible to colocate them with your GIS server.
To client applications, there is no difference between accessing GIS services directly or through the proxy. However, as the ArcGIS Server administrator, you may want to use a reverse proxy server for one or more of the following reasons:
Access GIS services over standard ports
When not using a reverse proxy server, clients will connect directly to ArcGIS Server through http://gisserver.domain.com:6080 or https://gisserver.domain.com:6443 if you have configured HTTPS. You cannot change the default ports used by ArcGIS Server. If you want client applications to use standard ports, such as 80 and 443 for HTTP and HTTPS, respectively, you'll need to configure a reverse proxy and direct clients to access services through it. For example, you could configure your reverse proxy at http://proxy.domain.com/arcgis or at http://proxy.domain.com/myGIS.
Isolate ArcGIS Server behind your organization's firewall
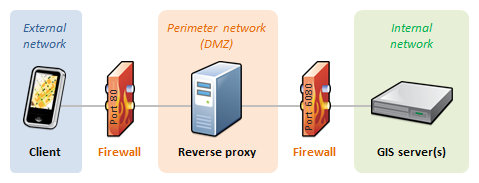
If you want to make your services and applications publicly available on the Internet, it is recommended to use a reverse proxy web server configuration to isolate ArcGIS Server behind your organization's firewall. In this configuration, incoming requests from the Internet pass through a firewall that blocks all ports except 80 and 443 (HTTP and HTTPS, respectively). Your reverse proxy web server receives the incoming request, passes it to ArcGIS Server through another firewall via port 6080 or 6443 (HTTP or HTTPS), and sends the response back to the client. The following diagram shows how the reverse proxy server would reside in a perimeter network, helping you control access to your secure internal network.
To learn how to integrate a reverse proxy server with ArcGIS Server, see Using a reverse proxy server with ArcGIS Server.
Block administrative access to your site
A reverse proxy server can be used to block access to specific resources in your site. For example, you can configure your reverse proxy to block access to ArcGIS Server Manager and the ArcGIS Server Administrator Directory. This is a good practice, especially if you expose your ArcGIS Server services to the Internet.
When using ArcGIS Web Adaptor, disable administrative access to your site by following the instructions in Configuring the Web Adaptor after installation. If you are using a third-party reverse proxy server, refer to its specific documentation to block access to all requests that attempt to access ArcGIS Server Manager (proxy.domain.com/arcgis/manager/) or the ArcGIS Server Administrator Directory (proxy.domain.com/arcgis/admin/).
While administrative access will be blocked when accessing your site through the reverse proxy, administrative access will still be available when accessing your ArcGIS Server directly through its default ports (6080 or 6443). Firewalls should be used appropriately to control where these ports can be accessed.
Leverage features in your own web server
Web servers include many features that you may want to leverage as part of your ArcGIS Server deployment. By sharing your GIS services through your reverse proxy server, you can leverage the logging, caching, and security features of your web server.
- Web tier authentication: By default, ArcGIS Server uses token-based authentication (often referred to as ArcGIS token-based or GIS tier authentication). Alternatively, you can choose to configure ArcGIS Server with web tier authentication. This method enables ArcGIS Server to delegate authentication to your own web server. For example, you can leverage HTTP basic, authentication with client certificates, and other standard authentication methods. If you need web tier authentication, you must use ArcGIS Web Adaptor. Web tier authentication is not available through a third-party reverse proxy web server.
- Logging: ArcGIS Server logs include information that is specific to ArcGIS Server services, for example, which operation has been invoked, the execution time of ArcGIS Server calls, as well as warnings and errors triggered in your GIS server. You can complement this information with logs from your web server, which provide details that may be absent in ArcGIS Server logs, such as the IP address from which the requests were made, the user agent, the referrer, and so on.
- Other features: Most web servers provide you with options to tightly control requests and responses. For example, you can apply filtering rules to incoming requests, block access from specific IP addresses or domain names, and so on.
Summary
ArcGIS Web Adaptor or a third-party reverse proxy server is an excellent complement to single-machine deployments of ArcGIS Server. Both provide additional security features. It is strongly recommended that you use one of them if you plan to expose your GIS services to the Internet, and it may be necessary even for intranet deployments, depending on your security requirements.
Advantages
- Complements the single-machine deployment with an extra level of security.
Disadvantages
- The use of a reverse proxy server can potentially add an overhead to requests to your ArcGIS Server services. This is especially true when leveraging web tier authentication for very large and complex (nested groups or federated) enterprise identity stores.
- Not highly available; the GIS server and reverse proxy server are single points of failure if either go offline. Refer to the Single-machine high-availability (active-passive) deployment for details.